Security & Privacy
The Easy Agile team takes security very seriously. We know that nothing is infallible and we are always working to improve our security practices, which are outlined below.
Find our SOC 2 Type II report, Data Processing Agreement (DPA) and more at trust.easyagile.com.
Storing app data securely
Easy Agile Programs is available on Jira Cloud, and on Jira Data Center.
Easy Agile’s cloud services are SOC 2 Type II certified.
For our Data Center apps, all app data is stored in your Jira database.
See Programs app data storage for more information.
Security Vulnerabilities
We align with the Security Severity Levels published by Atlassian. As a Platinum Atlassian Marketplace Partner, we adhere to their security requirements for Cloud applications.
We participate in the Atlassian Marketplace Security Bug Bounty Program.
If you believe you have found or experienced a security vulnerability with an Easy Agile product or service please raise a security incident.
Error reporting
Easy Agile products use error reporting service BugSnag to assist us in providing higher-quality software and quickly diagnose errors that occur in Easy Agile code running in the browser. No data is ever transmitted from your Jira server(s). This information helps us quickly pinpoint issues to help quickly resolve support requests, or ship fixes before support requests are raised.
No Personally Identifiable Information (PII) is included in the BugSnag payload events sent.
Key points
Only errors that originate from within Easy Agile code are transmitted.
All business-sensitive information is redacted, such as:
The URL of the Jira instance
Any project keys
Any issue keys
Usernames or any other personally identifiable information
We include the app Entitlement Number or Support Entitlement Number (SEN) in analytics to improve your customer support experience. For example, in the event you experience an error and raise a support request, we can diagnose the problem quickly. We also collect an anonymous and random unique identifier for each browser session, this unique identifier (UUID) is not tied to, or seeded from, a user's personally identifiable information.
How do I disable error reporting from Easy Agile Programs to Easy Agile?
To disable error reporting, disable the module “eap-load-analytics” as described below.
How do I disable the in-app “Welcome” video and signup form?
Disabling modules including the Welcome screen is only available on Data Center versions of the app.
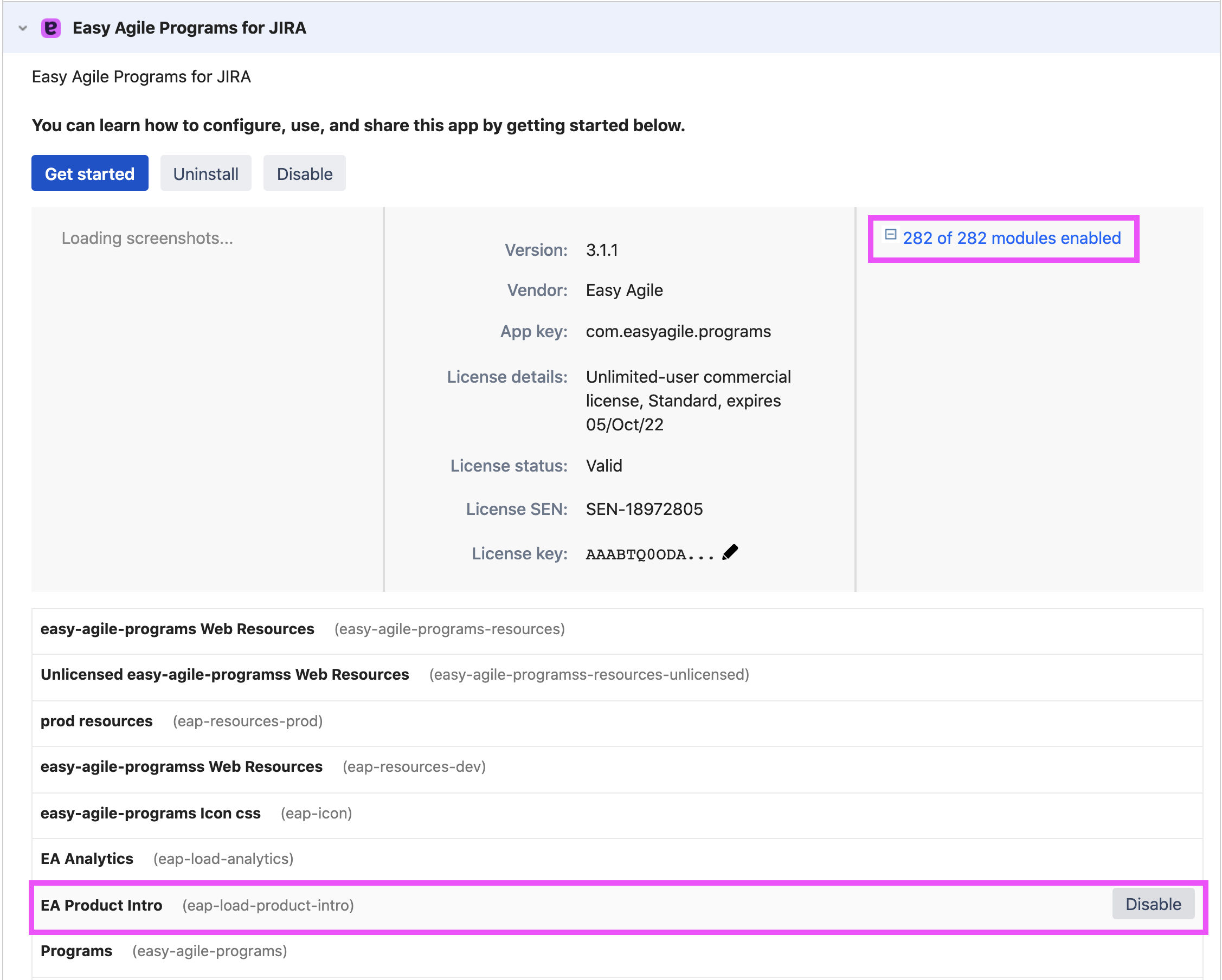
To disable the Product Intro, you will need to disable the ‘EA Product Intro’ module in the app.
Here are steps to walk you through this process:
Navigate to the 'Manage Apps' page under the Administrator menu
Navigate to 'Easy Agile Programs' from your list under 'User-installed apps'
To the right of the Programs listing, expand the 'Modules Enabled' dropdown
Find 'EA Product Intro' from the list of modules, and select 'Disable'
Analytics
What analytics does Easy Agile Programs capture and why?
Easy Agile captures analytics events from our products so that we can better understand how they are being used, and identify opportunities for improvement. The analytics data captured is stored in a private analytics database hosted by Amazon Web Services in the United States of America. This data is also sent to Amplitude, a third-party analytics platform to query and visualize analytics data to make informed decisions about product development.
For more information on how Amplitude stores this data see here.
No Personally Identifiable Information is captured in our analytics events.
To improve your customer support experience, the analytics data we collect includes the license Support Entitlement Number (SEN). This is so that we can more quickly and accurately diagnose problems when you raise a support request.
We also collect an anonymous and random unique identifier for each browser session. This unique identifier (UUID) is not tied to, or seeded from, personally identifiable information.
Example analytics event data we receive:
Add-on Key | SEN (Support Entitlement Number) | Action | Event Data | Timestamp | Version |
|---|---|---|---|---|---|
com.easyagile.programs | SEN-XXXXXXX | eap-rendered | {"route": "/plugins/servlet/eap/program/:programId/increment/:incrementId", "boardType": null, "isConnect": false, "eapVersion": "1.0.4", "browserName": "Chrome", "jiraVersion": "8.5.1", "screenWidth": 1920, "windowWidth": 1920, "loadDuration": 18849, "projectCount": 0, "screenHeight": 1080, "windowHeight": 937, "browserVersion": "79", "estimationType": "n/a", "screenFormatted": "1920x1080", "windowFormatted": "1920x937", "completeLoadDuration": 18849} | 2017-03-20 22:54:39.488+00 | 2.3.0 |
com.easyagile.programs | SEN-XXXXXXX | backlog-toggled | 2017-03-20 22:53:22.433+00 | 1.2.3-AC |
How do I disable the analytics events from Easy Agile Programs from being sent to Easy Agile?
Disabling modules including analytics is only available on Data Center versions of the app.
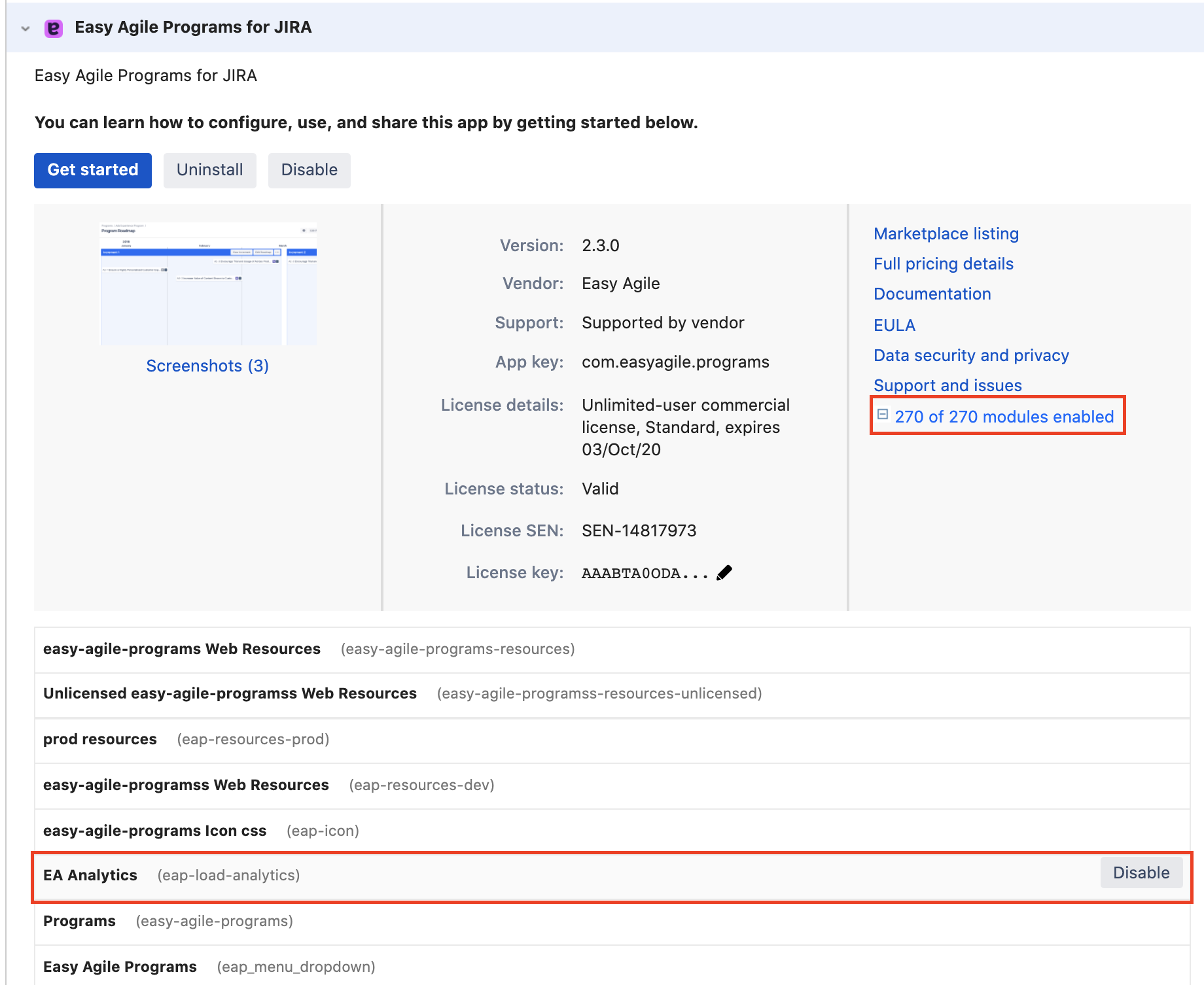
To disable analytics events being sent to us, you will need to disable the “eap-load-analytics” module in the app.
Here are steps to walk you through this process:
Navigate to the 'Manage Apps' page under the Administrator menu
Navigate to 'Easy Agile Programs' from your list under 'User-installed apps'
To the right of the Easy Agile Programs listing, expand the 'Modules Enabled' dropdown
Find 'EA Analytics' from the list of modules, and select 'Disable'
Where can I read Easy Agile’s Privacy Policy?
The Easy Agile Privacy Policy is available on our website at Privacy Policy.
